Telephony providers
General
Providers - service companies providing access to external networks. Internet, PSTN, etc. To access the PSTN, you must have a communications services agreement with one of these companies. Connection by providers is provided via various channels and protocols, e.g. E1 streams, analog lines, SIP, H.323. The platform works only with SIP protocol. If the provider can provide a SIP connection point, the platform connects directly to the provider. If not, intermediate nodes - gateways - are required. For example, from E1 to SIP.
Connection modes
The provider for a SIP connection provides: IP address or DNS name of the connection point, connection port (by default 5060). Further, depending on the connection method, the provider can provide either credentials - login, password, and optionally number, or the client address and subnet together with a separate connection. In the first case the client is registered from an arbitrary address, in the second case point-to-point - the client knows the server point, the server knows the client point. The mode with registration allows you to configure the redundancy of the platform nodes - if one goes down, the function of servicing the connection to the provider will be taken over by another.
Examples
Examples of credentials might look like this:
SIP-server: sipnet.ru Account: 71234567890 Password: 3y82lS5
Dedicated network: 172.27.103.88/29 (172.27.103.89 - default gateway, 172.27.103.90 - client equipment) IP server address: 44.55.66.77 Port: 5060 UDP The voice will go c 44.55.66.88 Both of the above ip addresses should be routed through the default gateway Codec: g711a 20ms Fax: transparent DTMF: rfc2833 Numbering range: 9991234567 - 9991234569 (3 numberf, 50 sessions) The "From" must necessarily contain a 10-digit number from the allocated range. The customer is expected to dial subscribers, i.e. local numbers are 7-digit numbers, zone and long-distance numbers - with "8-digit", international communication is closed.
Sometimes, as in the second case, it may be necessary to pre-configure the server network, add a vlan interface, address issued. Given that in this case the media gateway can be on any other server - to all servers where the first media processing point may be. And if this is not possible, it is necessary to configure a local media gateway bgmg on the esg server and work in media mode.
External PBX
The provider can be any external PBX that connects the platform "from below", i.e. as its subscriber. In this case, the setup is similar, and the connection options outlined above also take place. That is, an external PBX can be connected via registration (on the PBX), in point-to-point mode (mutual address setting is performed). But if it is necessary for the PBX to register with the platform, in this case the platform acts as a "provider" and the connection is made in a different way - through connecting as a subscriber.
Setting up a provider account.
Let’s assume that the rest of the domain is already configured and users can call each other.
In the domain, you need to configure provider account: link description of all properties. Customization can be done:
-
From the domain administrator’s workstation (Routing - Providers). In card mode, or in advanced mode via JSON (for access to specific fields).
-
Via Rest API (/rest/v1/uc/providers).
In the minimum mode, you need to set up:
-
User name (username) - the account name,
-
Password (pwd) - password,
-
Domain - a SIP server or a REGISTRAR,
-
Register (reg) - select the mode with registration or point-to-point.
-
Number of trunks - the number of licenses issued for the number of concurrent sessions. Optional:
-
Outbound proxy address (proxyaddr) - if different from the domain;
-
Outbound proxy port (proxyport) - if the port of the connection point is different from the 5060; Check:
-
Protocol (transport) - if different from the UDP;
-
Ping mode (pingmode), Ping server address (pingsrv), Ping interval, sec (pingtimeout) - if the connection is made via NAT with temporary port assignment.
We’ll look at the remaining fields as we go along below.
If a point-to-point connection is made, an explicit port for the client connection point can be set by the provider. This port must be configured in the configuration in the master domain for the ESG role instance to which account service should be bound. By default, in the configurations created in the configuration wizard, a port is assigned to esg 5080. In case different connections require many different ports - this can be solved either by multiplying esg instances or by using an intermediate gateway in the project that solves this problem.
Binding to microservices
Accounts are served by the microservice esg. If there is only one such microservice, the account will be served on it. If there are several, one random one will be selected from the available and active ones. In a point-to-point configuration, when esg microservice instances are spread across different servers, and the client address issued by the provider refers to only one of them, it may be necessary to explicitly bind the provider account to the esg microservice instance. This is done in the "esg role RoleID value (serveridxs)" field. See esg for details. Identifiers are given to microservices in the configuration.
All provider accounts across all domains are served on the same microservice instances by default esg. If necessary, you can split accounts into different instances, but then these instances must be multiplied in the configuration (in the master domain), assigning them different names and ports, and also prescribe the accounts in the domains explicit bindings to instances (field "RoleID value of esg role (serveridxs)"). This is usually not required.
Redundancy is only possible if multiple esg microservice instances are configured in the configuration and the account is not restricted to using only one of them. At any given time, an account is served by no more than 1 esg instance. When a server with a serving instance crashes, a failover to the next highest priority instance occurs within a few seconds. If a higher priority instance is restored, a failover back to the next higher priority instance occurs within a few seconds.
Viewing the registration status
The status of the account and its registration is available:
-
In the domain administrator’s workstation. (Monitoring - Providers). Only the status view is available here. But this mode uses a request to the API, in the body of the response to which there is also the provider’s SIP response.
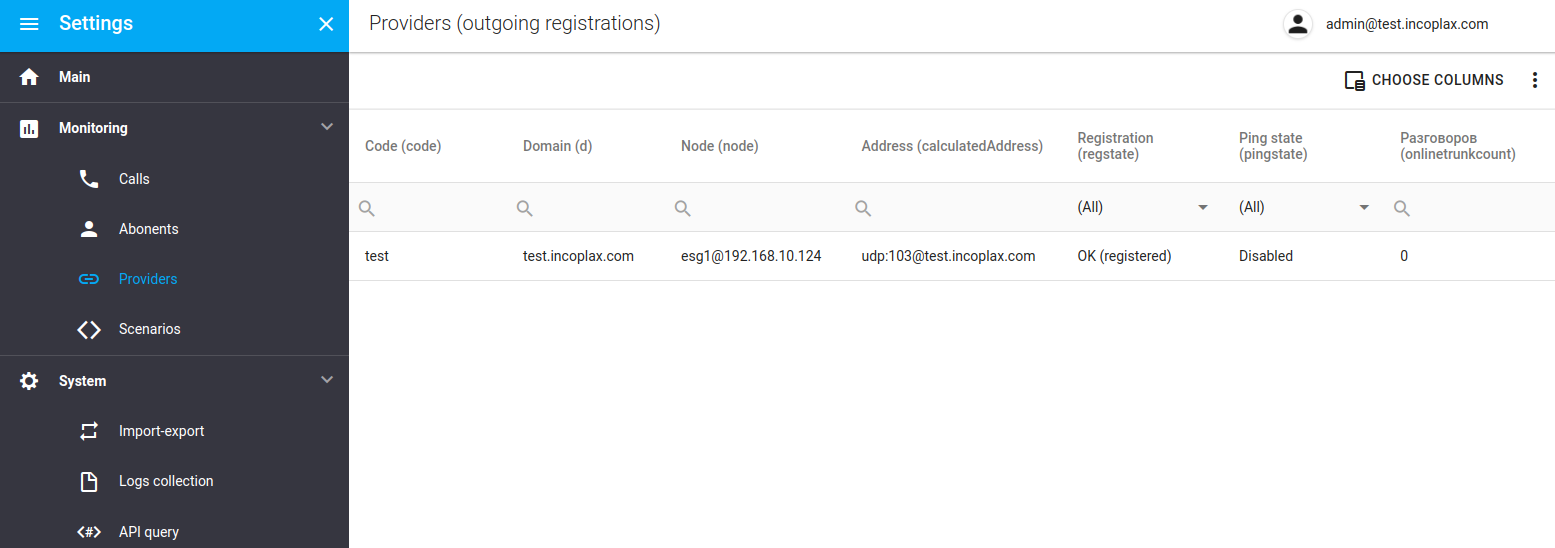
-
Via HTTP API:
/api/monitor/v1/esg/active?regs=true. Here is the status of the last response to the registration request, as well as the body of that response, and the number of active sessions.
{
"resultcode": 0,
"resultmsg": "OK",
"data": {
"sites": [
{
"site": "main_site",
"servers": [
{
"srvidx": 1005,
"node": "esg1@192.168.0.112",
"addr": "192.168.0.112",
"online": true,
"regs": [
{
"code": "pbx2",
"d": "test.okteller.ru",
"user": "provider",
"domain": "test.okteller.ru",
"port": 5060,
"proto": "udp",
"addrs": [
"test.okteller.ru",
"192.168.0.112"
],
"regstate": "registered",
"pingstate": "disabled",
"last_response": [
"SIP/2.0 200 OK",
"Via: SIP/2.0/UDP 192.168.0.112:5080;rport=5080;received=192.168.0.112;branch=z9hG4bK4DVwMd-2bcZ6H",
"From: <sip:provider@test.okteller.ru>;tag=3ZxqYI",
"To: <sip:provider@test.okteller.ru>;tag=rB2-0GE-3PP1",
"Call-ID: Z76iX6vyAeqyWKi9hEp5DHUJ3le",
"CSeq: 309187570 REGISTER",
"Max-Forwards: 70",
"Content-Length: 0",
"Contact: <sip:provider@192.168.0.112:5080>;expires=3600",
"Supported: path",
"Allow: REGISTER,INVITE,ACK,CANCEL,BYE,REFER,NOTIFY,OPTIONS,INFO,SUBSCRIBE,MESSAGE,UPDATE",
"Date: Wed, 05 Apr 2023 14:02:41 GMT",
"Path: <sip:r_Q4YyzUe@192.168.0.112:5060;transport=tcp;lr>"
],
"onlinetrunkcount": 0
}
]
}
]
}
]
}
}
-
Log: Server with esg microservice responsible for account service. Node logs folder,
sip/trn_*.log.
09:10:33.045 <0.682.0> Send to udp 192.168.0.112:5060 (ok) REGISTER sip:test.okteller.ru SIP/2.0 Via: SIP/2.0/UDP 192.168.0.112:5080;rport;branch=z9hG4bK4RfHQ7-aePz3y From: <sip:provider@test.okteller.ru>;tag=3ZxqYI To: <sip:provider@test.okteller.ru> Call-ID: Z76iX6vyAeqyWKi9hEp5DHUJ3le CSeq: 309187561 REGISTER Max-Forwards: 70 Content-Length: 0 Route: <sip:192.168.0.112;lr> Contact: <sip:provider@192.168.0.112:5080> Supported: path Expires: 3600 User-Agent: Era 1.8.3 Allow: INVITE,ACK,CANCEL,BYE,REFER,NOTIFY,OPTIONS,INFO,MESSAGE 09:10:33.049 <0.685.0> Recv from udp 192.168.0.112:5060 SIP/2.0 401 Unauthorized Via: SIP/2.0/UDP 192.168.0.112:5080;rport=5080;received=192.168.0.112;branch=z9hG4bK4RfHQ7-aePz3y From: <sip:provider@test.okteller.ru>;tag=3ZxqYI To: <sip:provider@test.okteller.ru>;tag=rB2-0GE-WH5X Call-ID: Z76iX6vyAeqyWKi9hEp5DHUJ3le CSeq: 309187561 REGISTER Max-Forwards: 70 Content-Length: 0 Www-Authenticate: Digest realm="b2b_1006__test.okteller.ru", nonce="KXapTShGqTzV5d0QAu7ddHRls9s", algorithm=MD5, qop="auth", opaque="1WVpoo" 09:10:33.060 <0.685.0> Send to udp 192.168.0.112:5060 (ok) REGISTER sip:test.okteller.ru SIP/2.0 Via: SIP/2.0/UDP 192.168.0.112:5080;rport;branch=z9hG4bK2w1opp-10Y8e1 From: <sip:provider@test.okteller.ru>;tag=3ZxqYI To: <sip:provider@test.okteller.ru> Call-ID: Z76iX6vyAeqyWKi9hEp5DHUJ3le CSeq: 309187562 REGISTER Max-Forwards: 70 Content-Length: 0 Route: <sip:192.168.0.112;lr> Contact: <sip:provider@192.168.0.112:5080> Supported: path Expires: 3600 Authorization: Digest username="provider", realm="b2b_1006__test.okteller.ru", nonce="KXapTShGqTzV5d0QAu7ddHRls9s", uri="sip:test.okteller.ru", response="e1a569e736485e2eed64af1990cf4727", algorithm=MD5, qop=auth, cnonce="auBMkM6dgdpbzM8neoqG1dxmndx", nc=00000001, opaque="1WVpoo" User-Agent: Era 1.8.3 Allow: INVITE,ACK,CANCEL,BYE,REFER,NOTIFY,OPTIONS,INFO,MESSAGE 09:10:33.072 <0.685.0> Recv from udp 192.168.0.112:5060 SIP/2.0 200 OK Via: SIP/2.0/UDP 192.168.0.112:5080;rport=5080;received=192.168.0.112;branch=z9hG4bK2w1opp-10Y8e1 From: <sip:provider@test.okteller.ru>;tag=3ZxqYI To: <sip:provider@test.okteller.ru>;tag=rB2-0GE-QA9Q Call-ID: Z76iX6vyAeqyWKi9hEp5DHUJ3le CSeq: 309187562 REGISTER Max-Forwards: 70 Content-Length: 0 Contact: <sip:provider@192.168.0.112:5080>;expires=3600 Supported: path Allow: REGISTER,INVITE,ACK,CANCEL,BYE,REFER,NOTIFY,OPTIONS,INFO,SUBSCRIBE,MESSAGE,UPDATE Date: Wed, 05 Apr 2023 06:10:33 GMT Path: <sip:r_Q19NAi5@192.168.0.112:5060;transport=tcp;lr>
The registration packet sent to the provider’s address and the provider’s response, as well as all other interactions - pings, invites, etc. - are available in their original form throughout the account’s activity in the log file.
Defense against attacks
If a server has an external address on the Internet, it is at risk. If it is possible to connect from arbitrary external addresses to the SIP port of the ESG microservice, it is an open area for attacks. Attacks are performed by external systems (sniffers) searching accounts. They send INVITE requests, substituting various values and authorization data. If the system starts to respond, the sniffer is activated and starts an intensive search of credentials in order to break into the number plan.
Protection against attacks is provided by a boundary filter. Permission checking is done based on border filter rules for incoming external SIP requests. Filter rules can be configured:
-
From the master domain administrator’s workstation (Routing - Filter). In card mode, or in advanced mode via JSON (for access to specific fields).
-
Via Rest API (/rest/v1/master/borderrules).
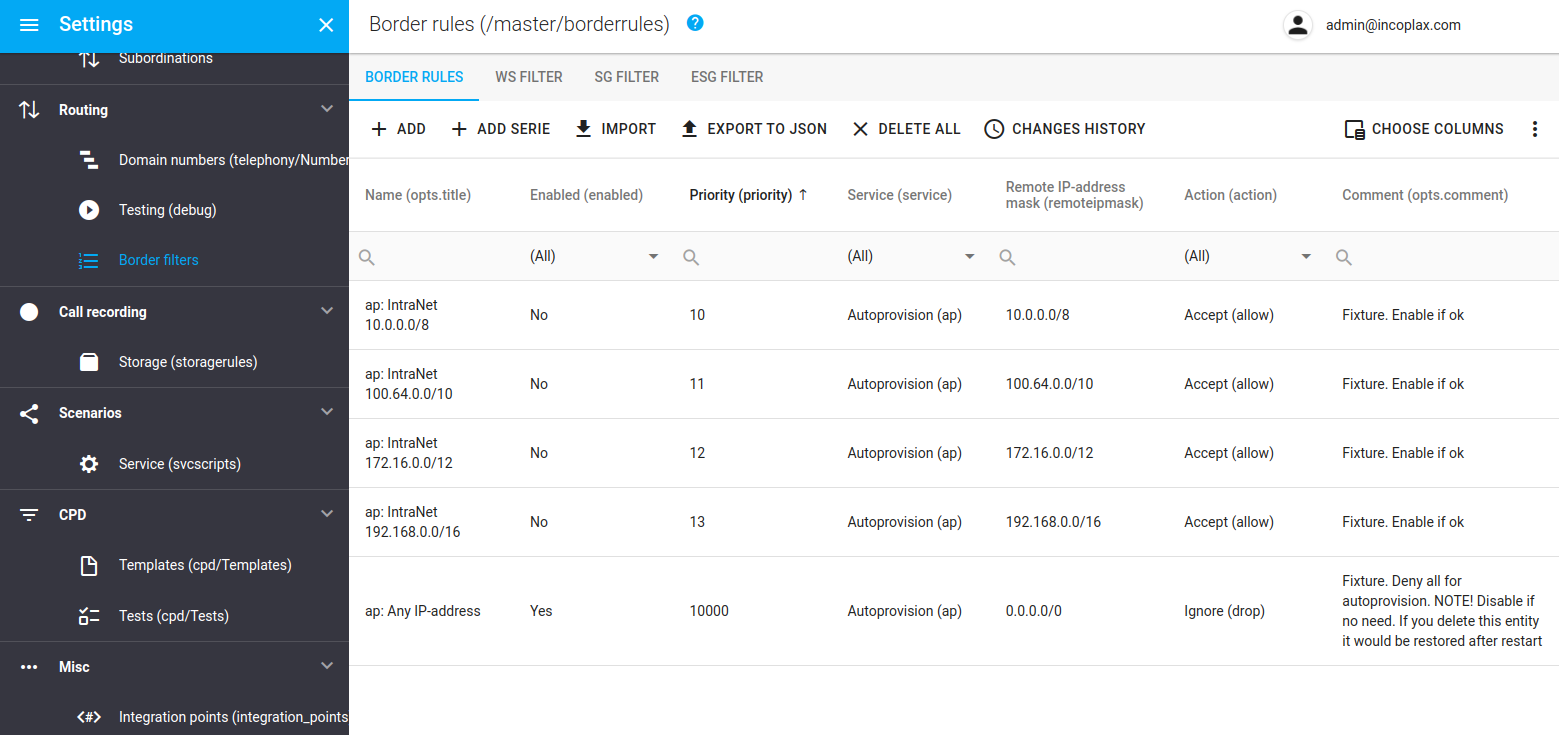
Rules can create black and white lists.
On closed networks, you may not configure a border filter, or you may configure blacklists.
In open networks, you should set up a whitelist, i.e. allow requests only from certain addresses and deny all other requests by the last priority rule. The deny mode should be set to 'drop' so that the server does not even respond to the incoming request and does not provoke external sniffers to continue to look for credentials.
If a rule has only a filter in the "address" field, such a request is not parsed and is processed directly on the socket. This is much more efficient than other modes.
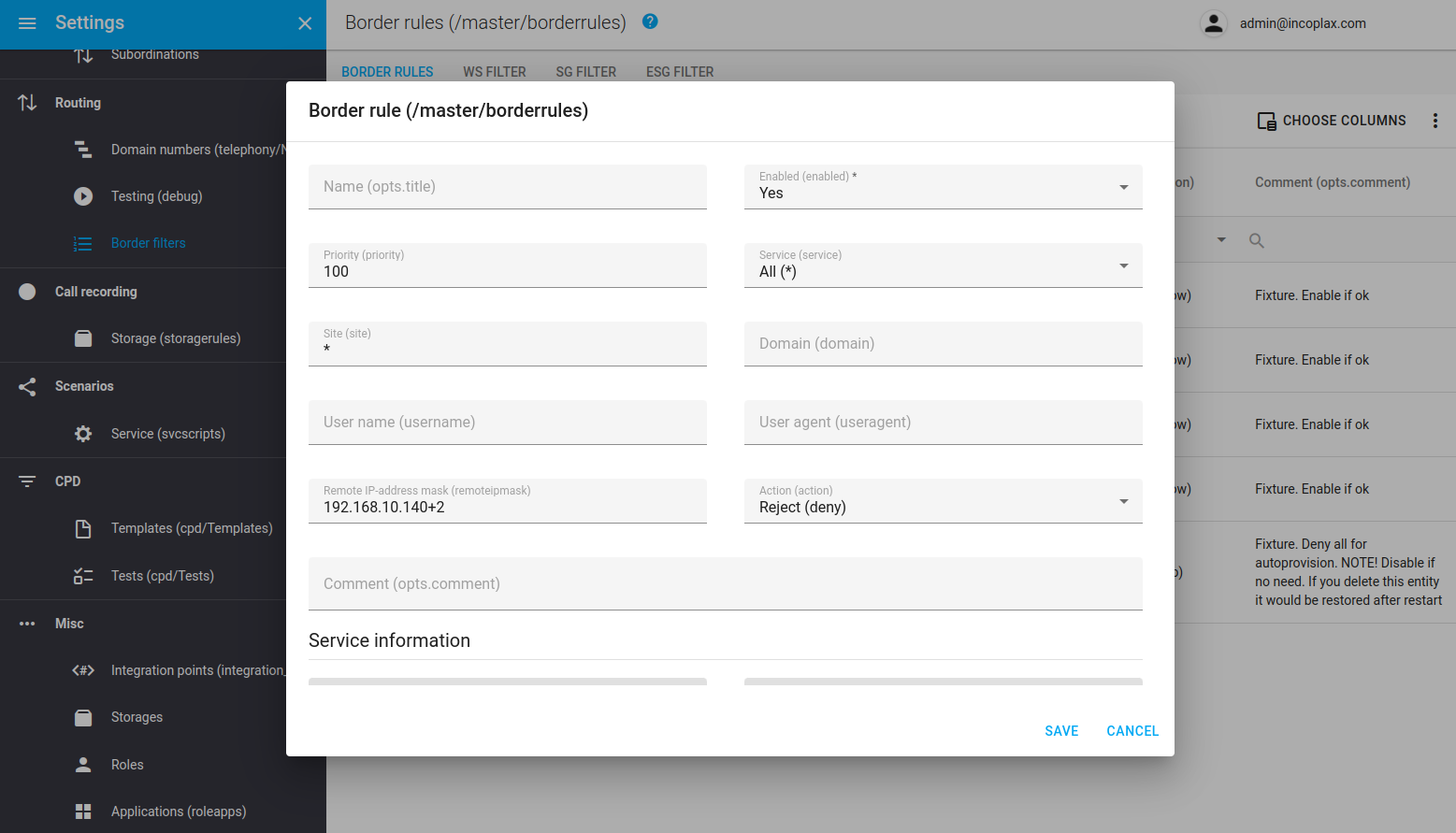
Thus, the most productive and efficient way to configure is a whitelist with allow rules on ip addresses and drop mode for all others.
In all other cases of setting filters - the SIP request goes through parsing, and after that other filters are checked and the action specified in the rule is applied.
Incoming call
When an incoming call (INVITE) arrives on the esg microservice port, it performs permission checking (discussed above) and binds to an account.
The account is searched among all provider accounts (across all domains) that are currently served by the instance esg.
13:26:57.450 <0.1128.0> Recv from udp 44.55.66.77:5060 INVITE sip:1234567890@172.27.103.90:5080;transport=UDP;user=phone SIP/2.0 Via: SIP/2.0/UDP 44.55.66.77:5060;maddr=89.232.125.56;branch=z9hG4bK-14c4dd7e-210137c8-fc50302 From: <sip:8430000000@44.55.66.77:5060;user=phone>;tag=5026-14c4dd7e-1087cebd-14c4dd7e To: <sip:1234567890@172.27.103.90:5080;user=phone> Call-ID: 40bb12f838738e5913c414c4dd7e210137c8da2fa8102e98aa28-0048-5988 CSeq: 1 INVITE User-agent: CS2000_NGSS/9.0 Max-Forwards: 63 Allow: ACK,BYE,CANCEL,INVITE,OPTIONS,INFO,SUBSCRIBE,REFER,NOTIFY,PRACK Contact: <sip:44.55.66.77:5060;transport=UDP> Supported: 100rel Content-Type: application/sdp Content-Length: 206 v=0 o=PVG 1357911604 1357911604 IN IP4 44.55.66.88 s=- p=+1 6135555555 c=IN IP4 44.55.66.88 t=0 0 m=audio 48970 RTP/AVP 8 13 101 a=rtpmap:101 telephone-event/8000 a=fmtp:101 0-15 a=ptime:20
When an INVITE request is received, active accounts are enumerated and conditions are checked. Two fields from the query are matched against two fields from the account. The search function takes two fields that are substituted sequentially in 6 steps from different headers up to the first discovery:
1. Search among accounts with registration:
1.1. username and domain are taken from the To header. In the example, these values are "1234567890" and "172.27.103.90".
1.2. username is taken from the To header, and domain is taken from the From header. In the example, the values are "1234567890" and "44.55.66.77".
1.3. username and domain are taken from the Contact header. In the example, these values are "" and "44.55.66.77".
2. Search among accounts without registration (point-to-point):
2.1. username and domain are taken from the Contact header. In the example, these values are "" and "44.55.66.77".
2.2. username is taken empty (""), domain from the Contact field. In the example these values are "" and "44.55.66.77".
2.3. username is taken from the To field, domain is taken from the From field. In the example, these values are "1234567890" and "44.55.66.77".
The search function itself checks the values passed in:
-
username - matching the account value in the 'username' field or one of the values in the list from the field 'opts.extusernames'.
-
domain - matching value: either the account domain field, or one of the external addresses of the server where the current esg is served, or one external NAT address. And the matching can be searched both explicitly, via masks (e.g., '44.55.6?.'), and via regular expressions (e.g., '44.55.6?.'), '/reg/^44[.]55[.]6\\d[.]\d+$').
If the account is not found as a result of the above algorithm, the server responds with '404 Not Found' and places a message in the Reason header "EB2B. Unknown account in contact".
In most cases, you don’t have to sort out the ISP connection, you just need to make an account and the calls start going through.
In complicated cases, when incoming calls fail and the system returns the specified message, you need to turn to the logs, find the incoming request there and analyze it. Based on the discussed algorithm, identify the cause of non-standard behavior. As a result, add settings to the account. For example,
-
Sometimes you should add username values to the 'opts.extusernames' field, which are regularly found in the query, and do not directly correspond to an account;
-
sometimes you should add domain values to the 'extaddrs' field that are regularly found in a query and do not directly correspond to an account. These can be specific addresses and masks, including regular expressions.
-
you should sometimes add external platform server addresses that the provider specifies in the domain field of the To header, as well as gray addresses from the settings, to the 'extaddrs' parameter of the ESG microservice in the configuration SIP-ALG
If the account is detected, the addresses matched to it are checked against the INVITE packet sender address (domain, proxy server address, domain name resolve results, address masks set in the account). If successful, the call is transferred to the service - creating a second arm towards the microservice b2b.
A common technique for complex customization:
-
Analyze multiple INVITE packets from different calls from the provider;
-
select headers To, From, Contact, and separate username and domain in their values - 6 fields are obtained;
-
Identify fields with constant values that clearly indicate the provider account (and not the subscriber or another provider’s account) and fields with variable values;
-
match the constant values with the verification algorithm above.
If the provider with registration specifies in the domain field of the To header of an INVITE request the external IP address of the server itself with ESG, and an unambiguous mapping of the provider account is made by username in the To header of incoming INVITE requests, then this address should be included in the list of 'extaddrs' parameters of the ESG microservice in the configuration (except if it is the only server address defined by the STUN request).
It is important to remember that when using the built-in SIP-ALG, white addresses will be spoofed to gray addresses, and account settings should take this into account. In the previous case, the gray address should be entered into the 'extaddrs' list of microservice settings ESG.
Outgoing call
To make an outgoing call through an ISP account, it should be routed to an external loop in routing rules of the same domain and specify the ISP account code.
Routing is done by a microservice b2b. Before sending a call to the corresponding esg account, its availability and the availability of the account are checked. If its state is inactive, if the set limit for simultaneous sessions is exceeded - routing goes to the next priority rule.
If there are multiple rules with the same priority, the sequence in which they are traversed is random each time. This can be used to distribute outgoing calls to two or more accounts.
Since the outgoing call comes to esg from inside, from the b2b microservice, the second arm is sent outward to the ISP.
Routing Configuration.
The esg microservice separates two number plans, an internal number plan and an external number plan (PSTN, or external PBX). There is probably a difference between these license plate plans. For example, there are 10-digit numbers on the outside and 4-digit numbers on the inside.
When calling across this boundary, the numbers mostly require modification.
Normalization rules (number substitution on esg).
Normalization rules can be bound to specific accounts (by identifier) or to a group (via masks for the code field), including the rule can be bound to all accounts by filling in the field 'providercode' = "*".
The objective of the normalization rules is to bring the incoming call initiator subscriber to the internal number plan and the outgoing call initiator subscriber to the external number plan. That is, the parameters of the INVITE call received at the ESG are different from the parameters of the INVITE call sent downstream. In between lies the normalization process. In particular, without using explicit normalization rules, calls are redirected with the following modifications:
-
incoming calls from the provider: From username - is not changed, To username - becomes empty, From domain and To domain - the domain of the system where the provider account mapped to the call is created is substituted.
-
outgoing calls from the system: From username - does not change, To username - does not change, From domain and To domain - provider’s domain specified in the account.
A common operation is to create a normalization rule for the outbound direction of an account with registration and substitute the account name as 'from username'. Without this, calls proceed with the number that was defined during routing in the internal number plan. A special case is the use of presentation rules, which pre-padded the external number for the caller based on complexly configured logic.
Thus, normalization rules are configured separately for the incoming direction and for the outgoing direction.
Normalization rules can be tested in the administrator’s ARM (Routing - Testing - Substitution).
Inbound itinerary.
Getting to b2b, the INVITE request has already undergone normalization and has a binding to the internal number plan. A call received from a provider can be routed in any way similar to other calls. Usually calls from ISPs are routed:
-
voice services (IVR);
-
in the KC queue;
-
for group rooms;
-
to personal internal numbers, if the number is marked as personal, or the tasks of the subscriber having the specified number include answering questions.
Obviously, they can be sent to other domains, redirected outward through other ISPs, or denied service.
Cshould avoid allowing dialing extensions (in IVR) and sending them to various services without verification and additional filters].
Outbound route.
To send a call to an ISP, rule should be configured in routing with the action 'external' and specifying the ISP code. The algorithm of behavior was discussed earlier in the section "Outgoing call".
Log Logs.
Logs related to the handling of telephony provider accounts are maintained by microservices esg. It is necessary to include in the configuration of the corresponding esg instance the parameter 'log_trn'. For extended logging it is necessary to set the TRACE logging mode in the nodes management section (Master Domain Administrator’s Workstation - System - Nodes) or DEBUG.
Log logs are in the directory specified during installation. The default path is '/opt/ERA_INSTANCE_NAME/log' in the host, and '/var/log/era' in the container. The full path to the esg logs directory might look like this: '/opt/ERA_INSTANCE_NAME/log/esg1@SERVER_ADDR/sip'
In the log 'trn_*.log' you can find all packets (across all ISPs). In the 'erl_*.log' log you can find detailed traces of the registration process.
Activity on all providers is placed in the logs. In debugging mode, it may be convenient to start a separate instance of a microservice with low priority (high value of the 'roleid' parameter in the configuration), bind the account under investigation to it (by setting the RoleId value in the account field) serveridxs).
Registration
For providers with registration to track the correctness of the registration process, you can look for REGISTER queries, for example:
09:10:33.060 <0.685.0> Send to udp 192.168.0.112:5060 (ok) REGISTER sip:test.okteller.ru SIP/2.0 Via: SIP/2.0/UDP 192.168.0.112:5080;rport;branch=z9hG4bK2w1opp-10Y8e1 From: <sip:provider@test.okteller.ru>;tag=3ZxqYI To: <sip:provider@test.okteller.ru> Call-ID: Z76iX6vyAeqyWKi9hEp5DHUJ3le CSeq: 309187562 REGISTER Max-Forwards: 70 Content-Length: 0 Route: <sip:192.168.0.112;lr> Contact: <sip:provider@192.168.0.112:5080> Supported: path Expires: 3600 Authorization: Digest username="provider", realm="b2b_1006__test.okteller.ru", nonce="KXapTShGqTzV5d0QAu7ddHRls9s", uri="sip:test.okteller.ru", response="e1a569e736485e2eed64af1990cf4727", algorithm=MD5, qop=auth, cnonce="auBMkM6dgdpbzM8neoqG1dxmndx", nc=00000001, opaque="1WVpoo" User-Agent: Era 1.8.3 Allow: INVITE,ACK,CANCEL,BYE,REFER,NOTIFY,OPTIONS,INFO,MESSAGE 09:10:33.072 <0.685.0> Recv from udp 192.168.0.112:5060 SIP/2.0 200 OK Via: SIP/2.0/UDP 192.168.0.112:5080;rport=5080;received=192.168.0.112;branch=z9hG4bK2w1opp-10Y8e1 From: <sip:provider@test.okteller.ru>;tag=3ZxqYI To: <sip:provider@test.okteller.ru>;tag=rB2-0GE-QA9Q Call-ID: Z76iX6vyAeqyWKi9hEp5DHUJ3le CSeq: 309187562 REGISTER Max-Forwards: 70 Content-Length: 0 Contact: <sip:provider@192.168.0.112:5080>;expires=3600 Supported: path Allow: REGISTER,INVITE,ACK,CANCEL,BYE,REFER,NOTIFY,OPTIONS,INFO,SUBSCRIBE,MESSAGE,UPDATE Date: Wed, 05 Apr 2023 06:10:33 GMT Path: <sip:r_Q19NAi5@192.168.0.112:5060;transport=tcp;lr>
Examples of failed registrations:
-
sending several REGISTER requests in a row with a growing pause between them and no response to them.
-
the word BANNED in the Recv string (for example:
15:00:11.042 <0.692.0> Recv from udp 192.168.0.112:5060 BANNED) - means that border filtering is enabled, but the sender address is not listed as allowed. If the address matches the one to which the server sent the REGISTER before, this is the reason.
Calls
A call is initiated by an INVITE request. To analyze what is happening with INVITE packets you should: detect the packet in the logfile, search for other packets of the session corresponding to it by Call-Id, find the answer. In case of a platform rejection, a Reason header revealing the details of the rejection can be found in the response.
If an outside call fails and no INVITE is detected, the following options are possible:
-
The word BANNED was detected - check ISP addresses for inclusion in border filters.
-
Unregistered account, the esg port is different from the port the ISP sends requests to. For example, the ISP sends to 5060, but the esg platform defaults to the esg port 5080.
-
You can use packet tracing, in which case the trace goes below the platform, in the operating system, and will be able to show the packets that actually arrive at the server. You can find the actual port in them as well. You can use the utilities tcpdump, tshark.
mkdir pcaps sudo chmod 777 pcaps sudo tshark -i eno1 -f "host 44.55.66.77" -w pcaps/trace.pcap ps ax | grep tshark sudo chmod 775 pcaps/trace.pcap rsync -avrh --progress pcaps/trace.pcap ... sudo rm -r pcaps
tcpdump -i any -nn -w temp.pcap
In any case, in case of any complications with call traversal, it is necessary to analyze SIP traffic. This is trn logs on all microservices serving the SIP: esg, b2b, sg, ivr, conf, prompt.
Diagram
In case the call reached b2b and a dialog was created, it can be detected in the Domain Administrator’s ARM (Monitoring - Calls).
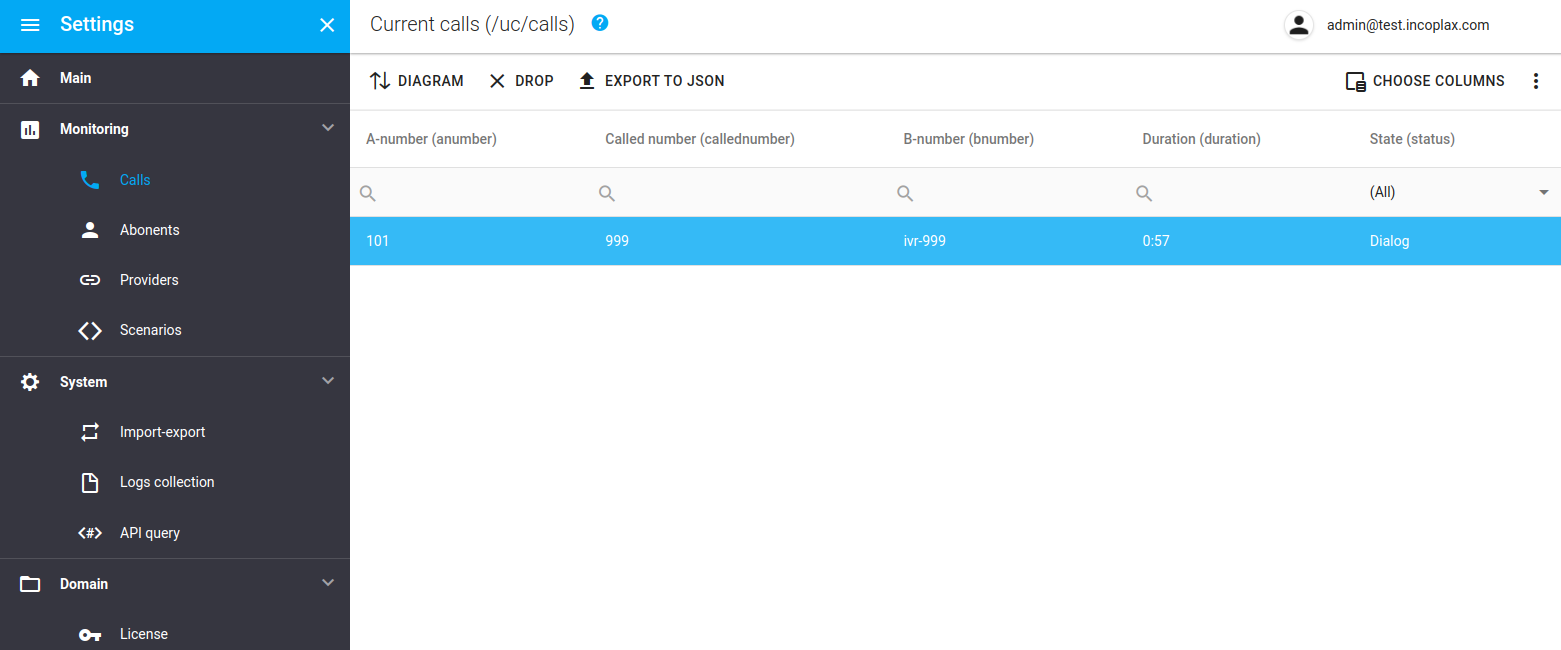
And when selecting with the cursor - perform the "Diagram" action. As a result, if trn-logs are enabled on the microservices through which the call passed, a sequence diagram with access to all packets related to the call will be displayed on the screen.
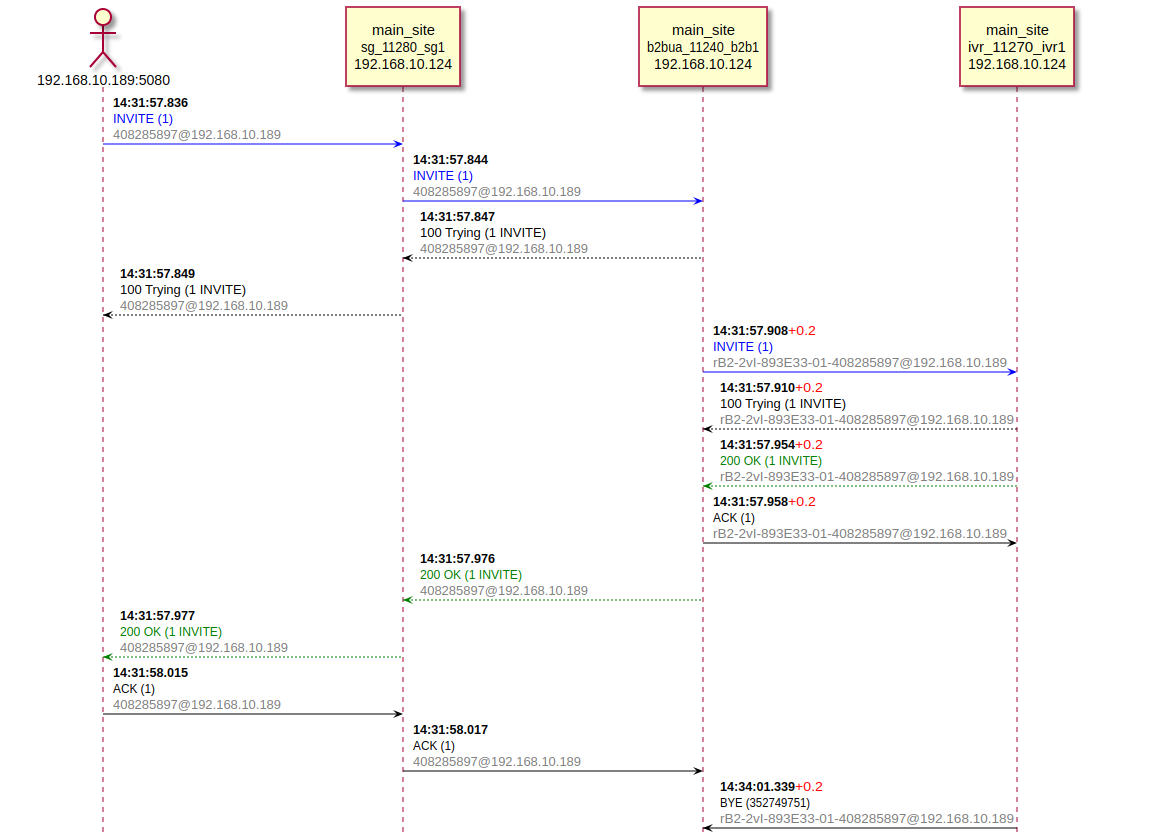
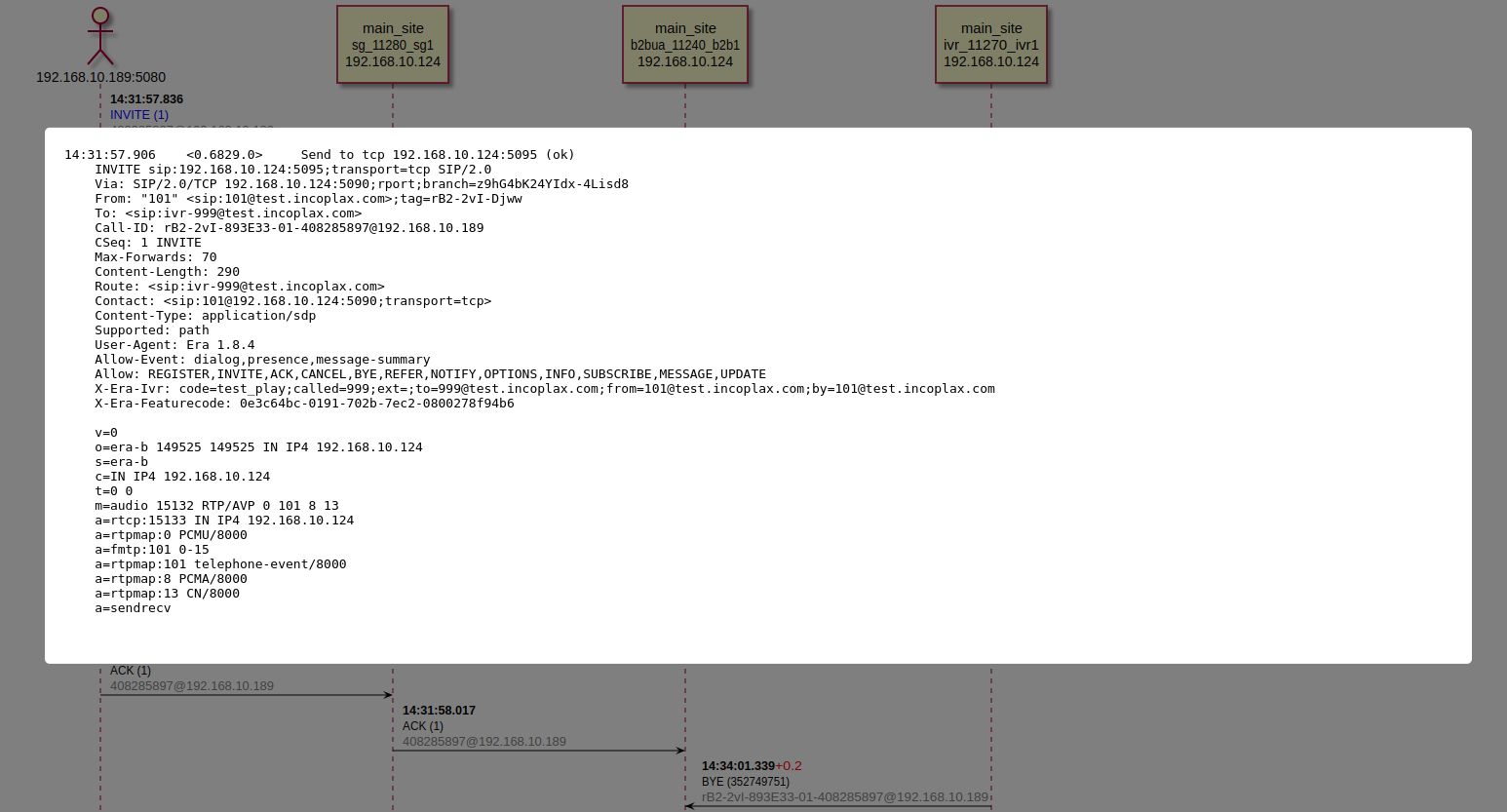
Logic esg
The esg logic corresponds to the b2bua (back-to-back useragent) mode. That is, each incoming call generates a dialog and a second arm. Esg to the second shoulder always generates a new Call-Id.
esg never broadcasts a REFER to another shoulder, but processes it locally, creating a new fork to the same side from whose shoulder the REFER request came. This ensures that the call is routed to the correct number plan. Correct means matching the number for the call transfer. This also means that the platform without additional modification cannot be configured to forward a call with out internal processing.
Each ISP account can operate in either Reinvite Probe mode, Local Media Processing mode, or both, but necessarily at least one mode.
Reinvite throw mode means that every session change is broadcast through esg to the opposite shoulder without change SDP.
Local media processing mode (field 'media'=true). Then it short-circuits all re-INVITE requests within the dialog, processing them locally by configuring media. This uses a bgmg media gateway located on the same server as the instance esg. This mode can be useful if you need to guarantee that media data is sent from the same address as the signaling SIP traffic to connect to the provider, or, for example, the number of addresses in the provider’s dedicated vlan subnet is narrowly limited and cannot be extended to all servers in the platform cluster. When using local media processing mode, signaling traffic can be terminated on a shoulder (reinvite=false) or broadcast to the opposite shoulder with a change in SDP (reinvite=true).
The default mode is reinvite=true and media=false, suitable for the vast majority of installations.
Registration on itself (testing)
It is acceptable for the provider to be registered on the platform itself as a subscriber device. Limited functionality testing can be done in this way. To bring a call in this case, you must call the extension under whose account the provider is registered. It can be either a different domain or the same domain.
This mode is used in particular when organizing load testing.
Due to the fact that esg completely replaces the CallId when sending a call to the other shoulder, there is no problem with parasitic loops.
Network interfaces and ports
Instances of esg, as well as other microservices responsible for SIP signaling, raise listeners on all interfaces (0.0.0.0). The ports are specified in the configuration for each individual microservice instance, but the ports specified refer to all interfaces of the corresponding server. This means that the platform without additional modification cannot be fine-tuned to listen for specific ports on specific interfaces.
In template configurations, ports are assigned to the esg role 5080, 5081. On these ports, listeners are raised on all server interfaces where the corresponding esg instance is executing, and UDP signaling protocol packets are sent from these ports.
There are instances where a particular ISP requires a port from a customer 5060. In this regard, port 5060 should be configured for esg. Then it may also be necessary to change the ports for instances as well sg. The only exception is when esg and sg instances are executed on different servers. In descending order of convenience, the following options are recommended:
-
Change the ISP requirements to allow the client to use the local port 5080.
-
Spread the esg and sg instances across different servers if there are enough of them, and use 5060 for both types.
-
Port change - 506X for esg, 508X for sg. Requires reconfiguration of all internal devices previously configured to connect to the server on the port 5060.
Utilization bgmg
The bgmg indication is just one of the situations in a multi-server platform deployment:
-
the subnet to which the provider belongs is not addressed from a portion of the servers in the cluster of the deployed platform (more specifically: from a portion of the servers that execute the mg);
-
the ISP requires matching client addresses for signaling traffic and media traffic.
For such providers you need to enable the mode media=true, reinvite=false. And to provide support for this mode, it is necessary to add a couple of bgmg instances to the configuration on the same servers where esg is executed (which, in accordance with the settings and placement of provider accounts, can serve them)
Work for NAT
Telephony providers overwhelmingly work with devices that connect from under the NAT. These devices are diverse, NAT settings are diverse, so in order to reduce the number of problematic situations, sending audio is usually done to the address and port from which the audio arrives on the port announced by the ISP in the SDP. This kind of behavior makes it impossible to notice problems with two-way audio passage.
If one-way audibility is observed in such a configuration, direct port mapping should be configured on the NAT. This may be required if:
-
Configured with an external PBX or ISP that does not support or is not configured to send RTP packets to the return address of the incoming sender RTP.
-
It should be possible to route an incoming call directly to an external number behind the same account.
The platform itself always redirects packets to the return address of the sender of incoming traffic. This algorithm shows its statistical superiority.
SIP-ALG
A special case of NAT is when a server from the outside is accessible by a white address that is not present among the local interfaces.
In this case, and possibly in some other cases, it is required to swap addresses in packets - local (gray) to external (white) in outgoing packets, and external (white) to local (gray) in incoming packets. To do this, you can use the SIP-ALG setting on the network router, or if this is not possible, configure this option in the instance settings esg.
Each packet that passes through an instance configured in this way will be subject to modification. Addresses will be spoofed according to the direction of the packet. For incoming packets, the modification is performed immediately after the SBC filter even before routing and number normalization. For outgoing packets, modification is performed after routing and normalization just before sending to the network.
The SIP-ALG configuration involves an unconditional 1-to-1 swap of the local (gray) address to the external (white) address. There can be several such bundles. For example:
"sip_alg": [
{"gray":"172.16.0.14","white":"62.85.127.4"},
{"gray":"172.16.0.15","white":"62.85.127.5"}
]